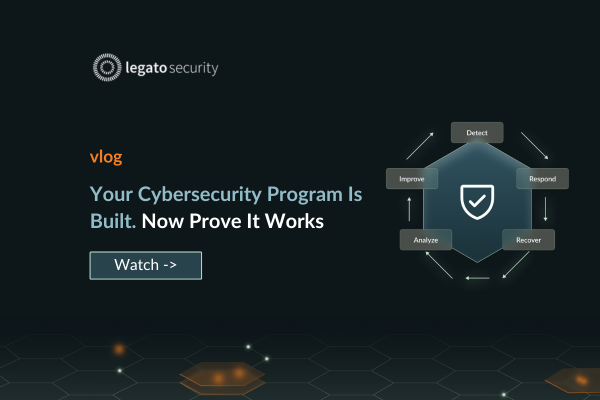
[ Insights for Cybersecurity Leaders ]
Empowering You with
Knowledge to Stay Secure
Explore expert perspectives, actionable insights, and practical strategies to navigate the ever-evolving cybersecurity landscape.
All Blog Posts
Thank you! Your submission has been received!
Oops! Something went wrong while submitting the form.
[ Stay in the know ]
Subscribe for Exclusive Insights Before They’re Available to the Public.
Get the latest in cybersecurity trends, threat intelligence, and industry updates delivered straight to your inbox.


.jpg)